Лимит на перевод с электронных кошельков могут поднять до 1 млн рублей
Концептуальных возражений по этому по поводу нет ни у ЦБ, ни у Росфинмониторинга
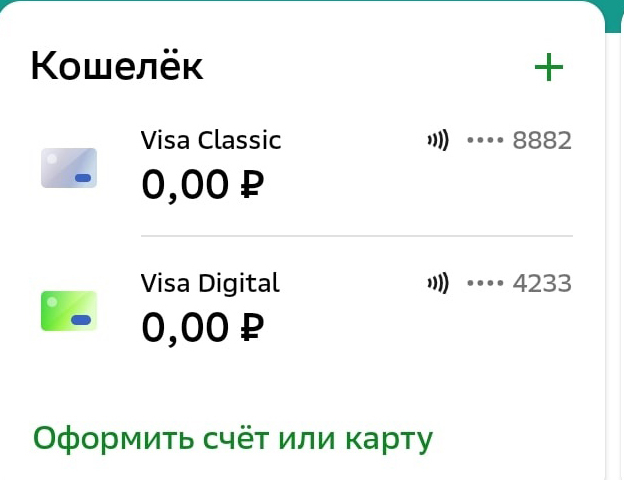
В России могут поднять с 600 тысяч до 1 млн рублей лимиты на остаток средств на электронных кошельках и максимальный размер перевода с них для граждан, прошедших идентификацию. С таким предложением к ЦБ РФ и Росфинмониторингу обратились участники рынка, рассказала «Известиям» председатель правления НКО «Мобильная карта» Елена Шейкина. По ее мнению, устаревшие суммы ограничений сдерживают развитие рынка электронных денежных средств (ЭДС).
Сейчас клиент с полным уровнем идентификации на электронном кошельке (ПЭСП, персонифицированное электронное средство платежа) может иметь остаток не более 600 тысяч рублей и такую же сумму переводить за один раз максимум. Однако это пороговое значение было установлено в 2014 году, а за прошедшее с того момента время инфляция составила около 90%, пишет издание.
В ЦБ подтвердили, что соответствующая инициатива к ним поступила. По мнению регулятора, это может способствовать повышению привлекательности услуг по переводу ЭДС для клиентов.
Концептуальных возражений нет и у Росфинмониторинга, сообщили «Известиям» в пресс-службе ведомства. Одновременно, по мнению Росфинмониторинга, такое увеличение фактически сближает функционал электронных кошельков с банковским счетом клиента. Поэтому, как подчеркнули в ведомстве, идентификацию и функционирование таких кошельков «целесообразно унифицировать с действующими антиотмывочными стандартами в отношении банковских счетов, в том числе, например, в части установления требования о личном присутствии клиента при предоставлении ПЭСП».
В 2022 году ЦБ повысил лимит с 600 тысяч до 1 млн рублей по операциям, подлежащим обязательному контролю, а также по максимальной сумме перевода через систему быстрых платежей (СБП). В феврале 2023 года первый зампред ЦБ Ольга Скоробогатова сообщила, что ЦБ рассмотрит изменение лимита для бесплатных переводов через СБП. «У нас есть такой запрос, мы к нему позитивно относимся, мы думаем на эту тему», — сказала она. Кроме того, в июле 2023 года стало известно, что власти хотят повысить лимит бесплатных переводов самому себе до 30 млн рублей.
Источник: https://frankmedia.ru/142509
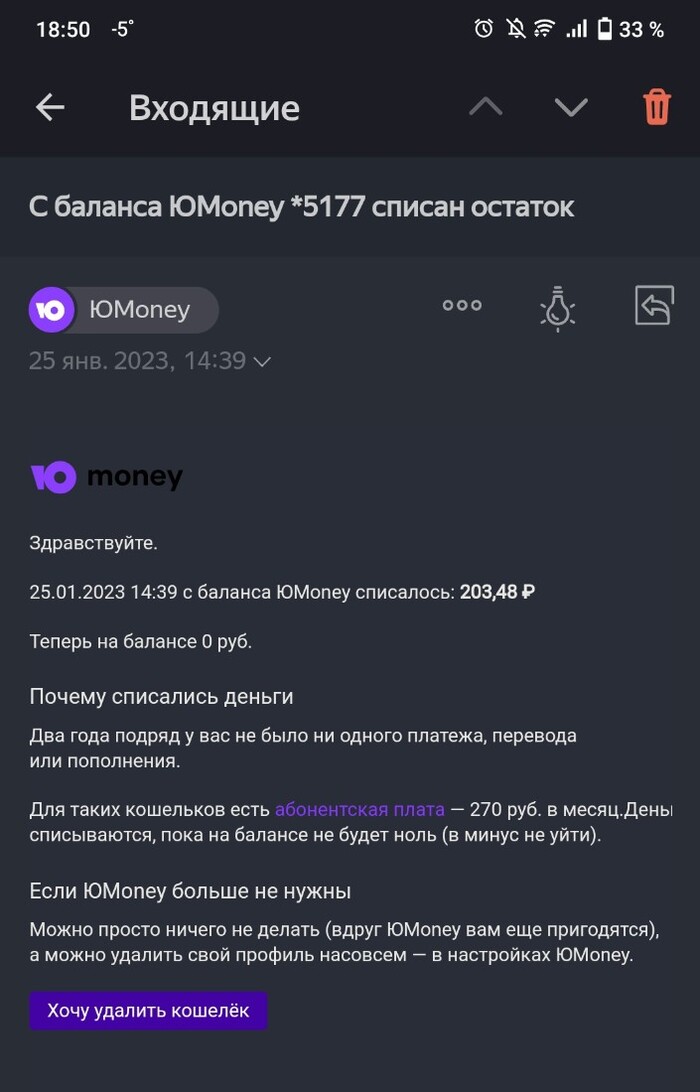
Новый развод от Юmoney?
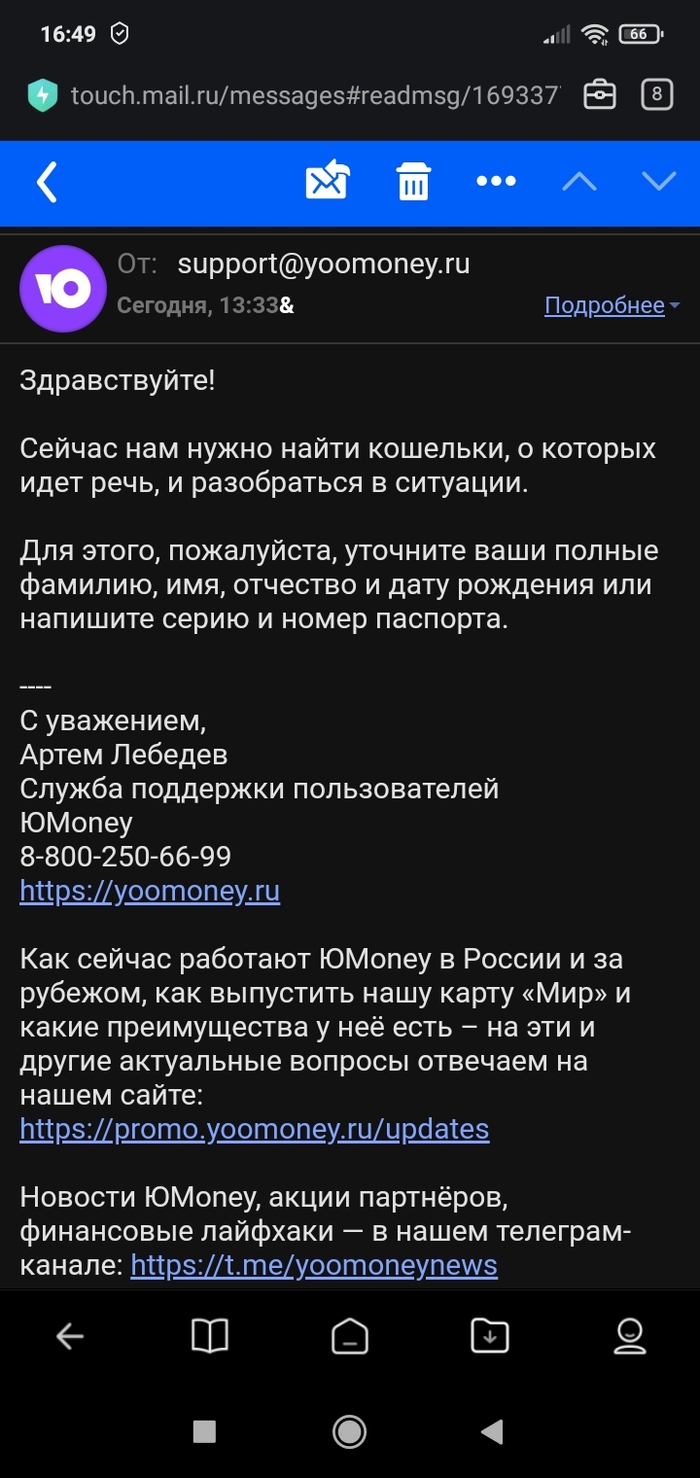
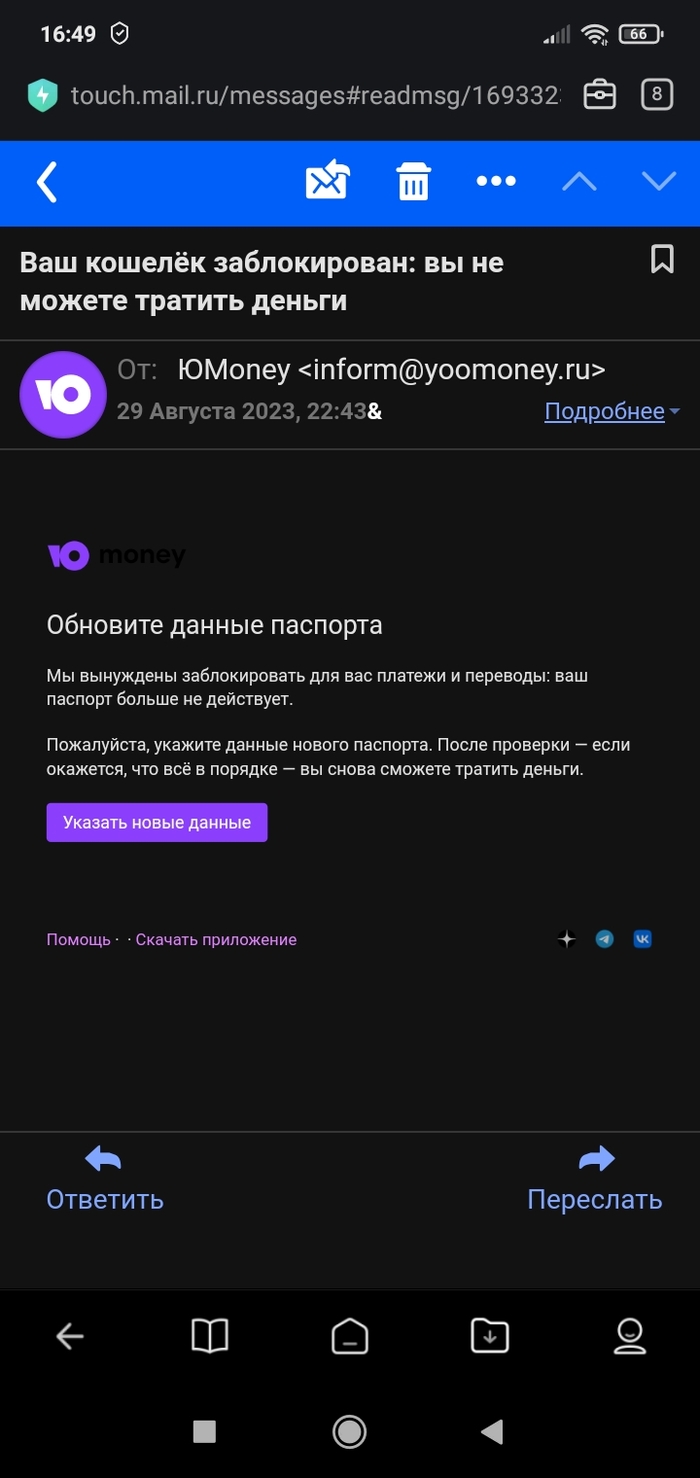
Сегодня пришло на почту, что все мои кошельки на Umoney заблочены, так как паспортные данные устарели. Всё бы ничего, но я никогда не регистрировалась на Umoney! Решила написать в их поддержку и в итоге от меня потребовали паспортные данные (ФИО, серия и номер паспорта) для уточнения информации. Естественно, я их не дала. Что это за новый вид развода? Кто-нибудь уже сталкивался с подобным? Раннее пыталась позвонить на горячую линию, но там тоже тишина.
Юmoney списывает деньги
Захожу сейчас на Яндекс почту и вижу письмо:
Сначала подумал, что фишинговое сообщение, проверил почту, вроде всё верно.
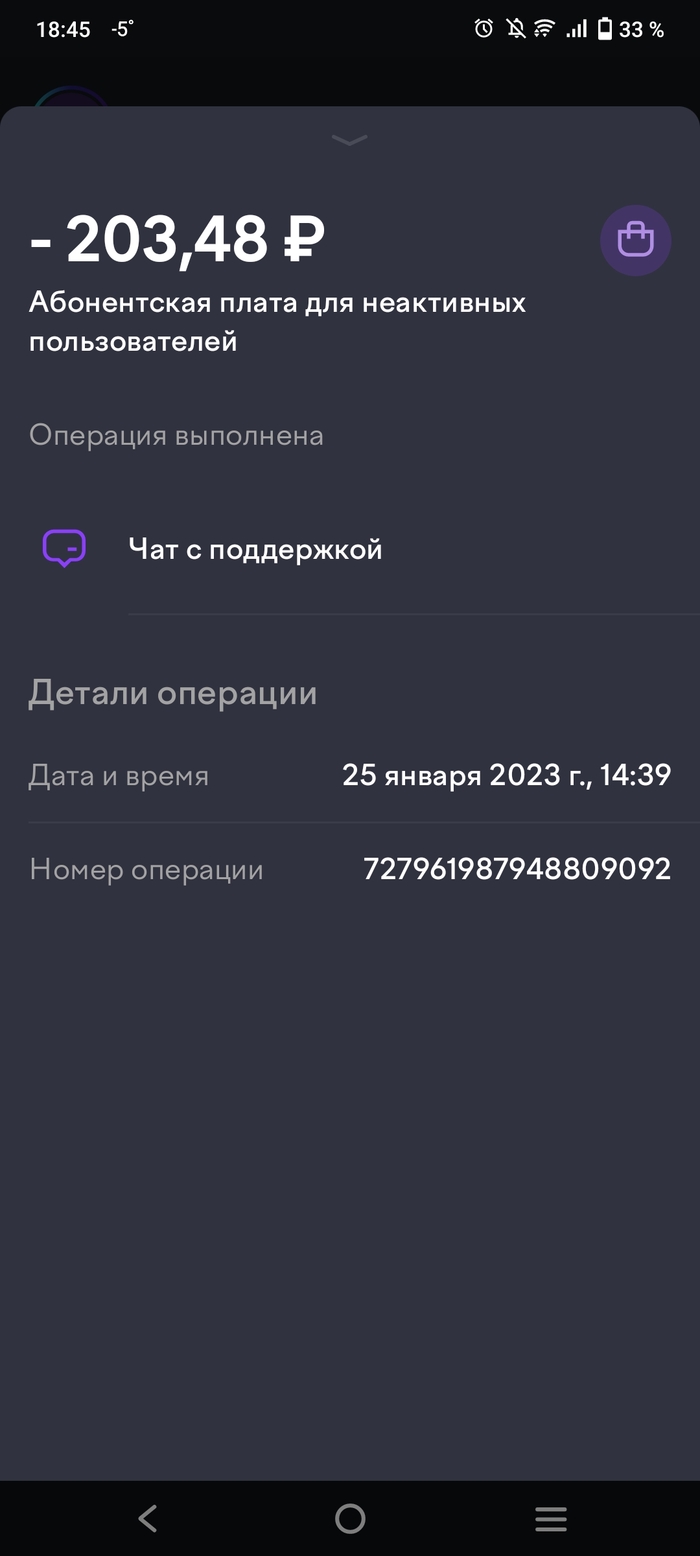
Скачал их приложение, действительно, эти нехорошие люди списывают средства с кошельков, кто ими давно не пользуется.
У меня в общем, нет слов. Короткая переписка с тех.поддержкой результатов не принесла.
@Sber, вы там совсем охуели???
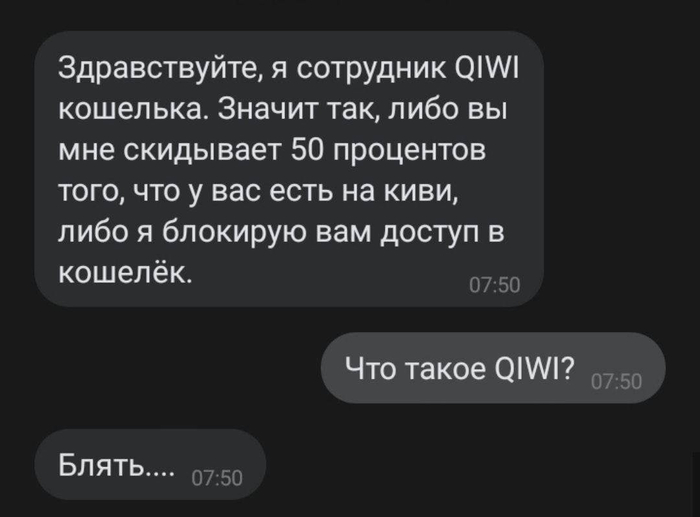
Удаляю ваш шляпный кошелёк.
Вы выбрали самую короткую дорогу к краху.
Всех пользователей Пикабу призываю удалять кошельки Юmoney и больше ими не пользоваться.
Что тут ещё можно сделать?
Холодные и Горячие кошельки находим уязвимости и устраняем различные атаки на Блокчейн
In the last article: “Blockchain Attack Vectors & Vulnerabilities to Smart Contracts” we reviewed all known attacks on the blockchain, in this article we will talk about crypto threats again and we will talk about identifying vulnerabilities for Cold wallets, as well as for Hot wallets. Blockchain is the underlying tech layer made up of a decentralized ledger, and a very secure data structure as there are a lot of distributed nodes that participate in the consensus algorithm. In order to hack the blockchain, hackers should exploit vulnerabilities in a lot of decentralized nodes.
The basic security assumption of blockchain is that it is impossible to hack so many nodes to change the state of the blockchain.
If blockchain tech is so secure, how could it be hacked?
The Achilles Heal of the technology is the centralized nature of institutional users that manage large amounts of crypto assets (money) for their clients, while the only thing that stays between the money and the hackers is the private key. The private key should be used to sign, on blockchain transactions, the same way that a manual signature could be used to sign traditional checks. If someone steals the institutions’ private key they can create a transaction on their behalf and steal the money. Unlike bank systems – once a hacked transaction is created there is no way to reverse it – the money is literally stolen.
Why is it important to store and safeguard your private key?
Whoever holds the private keys has complete control over the assets associated with that key. Because blockchain transactions are instantaneous and irrevocable, users aim to keep their private key secret. The private key is only generated once, so misplacing a private key effectively renders useless all the crypto assets associated with that address.
Although the optimal custody scenario has yet to be defined, it is undisputed that control of the private key is of paramount concern. In fact, the private key is, in essence, the real asset. It’s intrinsic properties and powers mean there is no way to truly safeguard it without exception.
Cold wallets “The vault of institutional custodians” are hardware devices that store Bitcoin or other cryptocurrencies initially, internet isolated, device. In theory, the cold wallet solution is reported to be the most secure way to store cryptocurrency. Some cryptocurrency users prefer to keep their digital assets in a physical “wallet,” most often a device that looks like a USB stick; they can only be accessed by being plugged directly into a computer and require an internet connection in order for a user to access and move their cryptocurrency funds.
There are several popular cold wallets for commercial use such as Trezor, Ledger Nano S and for enterprise and institutional investors some other devices use a combination of:
USB
Ethernet
SD card
External thumb drives
Dedicated air gapped machine with HSM
Problems associated with the above hardware is usability and to gain access to the crypto asset you need to connect the cold wallet to a computer and therefore it is exposed to the internet. By doing so you are compromising the cold wallet system through the Internet connection, thus exposing it to potential attack vectors and eventually potential cyber theft.
Using cold wallet storage is a necessary security precaution, especially when dealing with large amounts of Bitcoin and other crypto-assets. For example, a cryptocurrency exchange or crypto fund custodian would typically offer instant withdrawals and might be responsible for hundreds of thousands of Bitcoins and other crypto assets. To minimize the ability that hackers could steal the entire reserve in a security breach, the financial services operator would follow a standard protocol, by keeping the majority of the reserve in cold storage, while holding a smaller percentage of the assets available for day to day trade activity.
Essentially they would not store the majority of digital assets’ private keys on their server or any other connected computer. The only amount kept on the server is the minimum required to cover anticipated customer withdrawals.
Methods used to secure private keys for digital assets:
Data encryption that protects wallets with a strong password
Backups for digital wallets in case of computer crashes or fraud
Cold wallets are not truly secure as, at some point, they need to send funds and by doing so they rely on bi-directional communication and are connected to the internet. This is when they can be compromised and be infected with malicious data and extremely vulnerable to attacks. Therefore all cold wallets become hot wallets dispelling the theory of total security for institutional custodians.
Hot wallets today have an important role as they are capable of providing easy access to funds and processing automatic transactions, however private keys of the hot wallets are stored in a method that requires that they are always connected to the internet. There are different type’s of hot wallets that take a different approach on how to store private keys. In mathematical perspective, some duplicate private keys between different participants and other divide a private key between the participant. In other words, hot wallets today tackle the security risk by distributing private keys.
The Hot wallets participants maintain control of their private keys, so the cryptocurrency assets in the hot wallet remain under the holder’s control. However, the assets remain vulnerable to hacking, as a malicious person or group which gains access to your computer or smartphone would theoretically also be able to drain your wallet via getting access to the private key.
Hot wallet’s primary advantage is that it can be used for automatic and fast access transactions. Individuals looking to actually make purchases with their cryptocurrency assets might choose to use a hot wallet, for instance, as the holdings in that wallet can be transferable across the internet and in general, the number of crypto assets is at a high enough value, therefore it is not worth the time and money that hackers would invest to steal. On the other hand, hot wallets are definitely vulnerable to security breaches as they have ongoing access to the internet.
Different types of hot wallets all store the private keys on internet connected applications:
Basic Hot wallet – Direct connection of the private key on the Internet
Multisig Native Wallet – duplicates private keys – you only need to compromise two participants in order to gain access
Multiparty computation (MPC) – Distributes private key between 2-5 participants
If we look at the Multisig method even with 2-3 people or entities having to confirm a particular transaction, hacker groups will spend millions on institutional targets and they only require attack vectors for 2 out of 3 in order to compromise the security. Hacker groups are willing to do this as they stand to gain hundreds of millions in stolen crypto assets.
Using the above solutions could essentially prevent a rogue employee from stealing keys on-site, or from a cold-storage facility, or from any hardware device managed entirely by the company. There are mpc wallet providers that try to limit an attacker or a rogue employee from entering a single network and collecting all of the cryptographic information they would need to authorize and sign an illegal transaction, however, this solution is also not 100% secure and merely mitigating attack vectors is just not an option when billions are at stake.
Why should the industry care?
As of writing this article the total market cap for cryptocurrencies has exceeded $218 billion and is now in the 10th year of existence. In this past 10 years there have been many notable hacks. All institutions with custody of large amounts of crypto assets have a responsibility to their investors to ensure the most robust security options are deployed throughout their enterprise.
Furthermore, the hacks also lead to various other cyber damage
Theft of assets – irreversible
Reputation damage
Theft of private customer data
Loss of jobs
Closing down the business
But that’s a different article…
Although there is a lot of volatility in the market which in part is driven by FOMO and media hype, it is critical to acknowledge that a major factor is the security of digital assets and this can affect the value of a cryptocurrency or an exchange asset valuation fundamentally altering the entire ecosystem.
Key Takeaways:
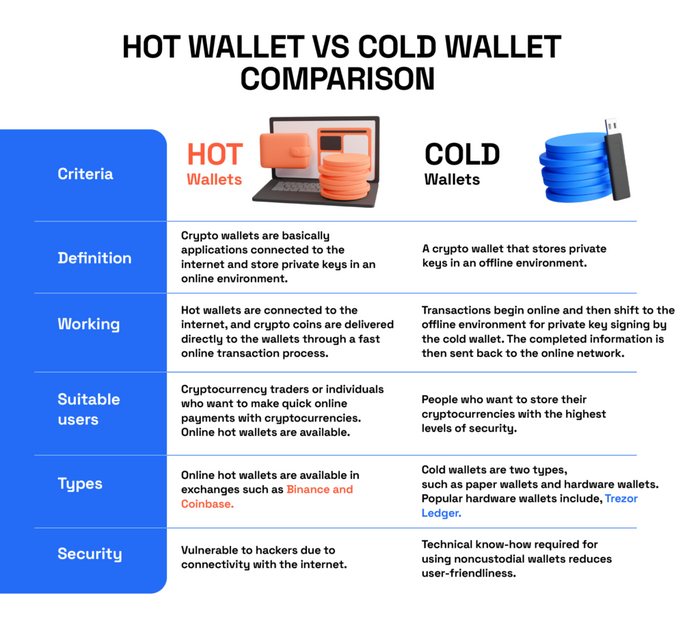
A hot wallet is always connected to the internet; hence it’s prone to online attacks – but it’s more convenient for daily use.
A cold wallet is mostly not connected to the internet; hence, it’s less prone to online attacks – but it’s less convenient for regular use.
When choosing a wallet, you should consider the security, convenience, fees, supported coins, and insurance factors.
If you are planning to buy digital assets, deciding how and where to store them is not an option, it’s a necessity. Unlike fiat currencies, cryptocurrencies live on the blockchain and require a proper storage platform known as a wallet. These wallets give you access to your crypto holdings through public and private keys.
You use a public key to send and receive cryptocurrencies and a private key to confirm transactions and prove ownership of a crypto wallet. You can think of your public key as your bank account number and your private key as your pin. The main difference between hot vs. cold wallets is that the former stores private keys online while the latter stores them offline.
This article takes a deep dive into the hot and cold wallet debate, considerations when choosing a wallet, and using both hot and cold wallets to manage your crypto portfolio.
What is a Hot Wallet?
A hot wallet is a software wallet that stores public and private keys online. You can access it through your computer or smartphone when connected to the internet. Hot wallets are more convenient for daily use as you don’t have to plug them in and out to use them – you just need an internet connection. They are also typically free to download and use, complete with a user-friendly interface that makes it easy for anyone to get started.
Hot wallets are vulnerable to attacks because they store public and private keys online, which exposes you to risks like phishing and other scams.
Types of Hot Wallets
There are two types of hot wallets – exchange-based, where a user opens an account with a centralized exchange that acts as the custodian of the users’ funds in their care, and non-custodial software hot wallets.
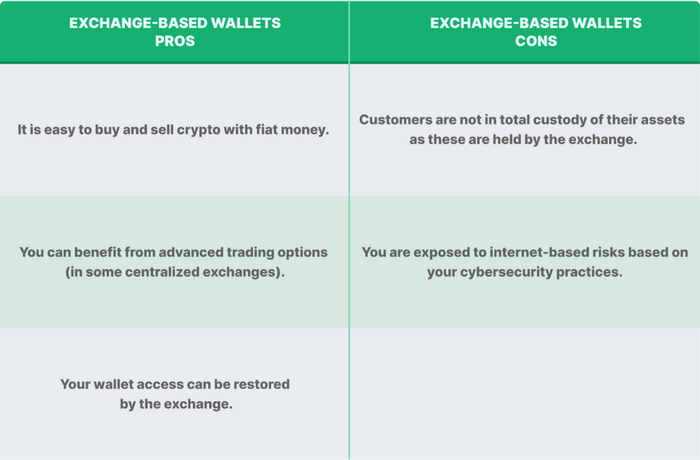
Exchange-Based Wallets
Exchange-based wallets are part of a centralized exchange. Centralized exchanges are custodial institutions that hold the private keys to their users’ addresses. This means that customers of such custodial financial platforms are not in total custody of their assets, as these are deposited into hot and cold wallets held by the institution.
Unfortunately, this exposes users to the risk of the exchange engaging in certain activities that result in the loss of customers’ funds, as seen in the case of FTX in November 2022. Moving forward, there is an industry wide push for more transparency and to hold custodial institutions accountable for their customers’ tokens with the introduction of Proof of Reserves.
While there is an overall drop in centralized exchange activity, exchange-based wallets are still popular, especially with retail investors, as they make it easy for users to buy and sell cryptocurrency with fiat money. Also, in the event you lose your log-in details, access to your wallet can be restored by contacting the exchange’s customer service.
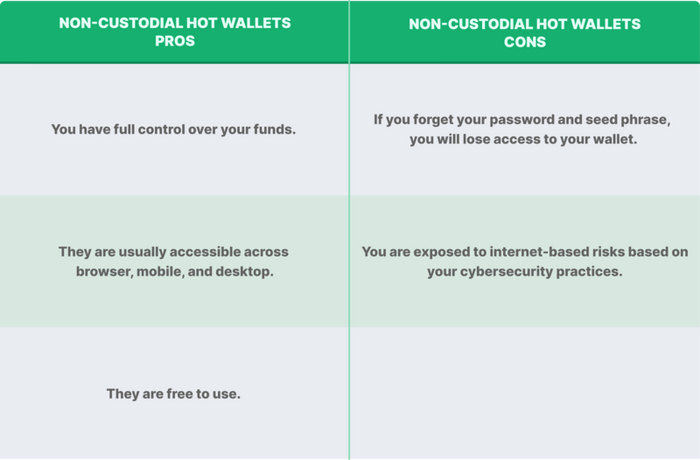
Non-Custodial Software Hot Wallets
Non-custodial software hot wallets can be accessed through mobile, browser or desktop applications.. Most of the time, they’re available across all three. In the case of these hot wallets, users are responsible for their own private keys and have full control over their funds. While this means your funds are safe in the event of a bank run, as they’re not stored in a custodial institution, if you lose your seed phrase, you will no longer be able to access your wallet and the crypto stored within.
What is a Seed Phrase?
When it comes to storing your seed phrase, don’t just write it on a piece of paper, which will fade over time or possibly be destroyed by water and fire. Instead, use crypto steel to record your seed phrase, and make multiple copies as backup.
Never store your seed phrase on a password manager or anywhere online or on your devices. That includes not taking a photo of it, or putting it in a google doc or note.
Examples of Hot Wallets
MetaMask – Best for Exploring the Ethereum Ecosystem
MetaMask is one of the most popular hot wallets in the crypto space and supports all EVM-compatible tokens. It’s easy to use and is available on desktop and mobile devices. Besides, it has extra in-built features for swapping, sending, and receiving crypto and collecting non-fungible tokens (NFTs) across networks.
Exodus – Best for Desktop
Exodus is the best hot wallet for desktops due to its high transaction speed, ease of use, and diverse client functionalities it provides. It’s one of the most visually appealing and intuitive wallets in the crypto space. It started as a desktop-only wallet but has expanded to support mobile devices. However, the Exodus desktop app for Windows, Linux, and Mac operating systems, is still the wallet’s primary offering.
What is a Cold Wallet?
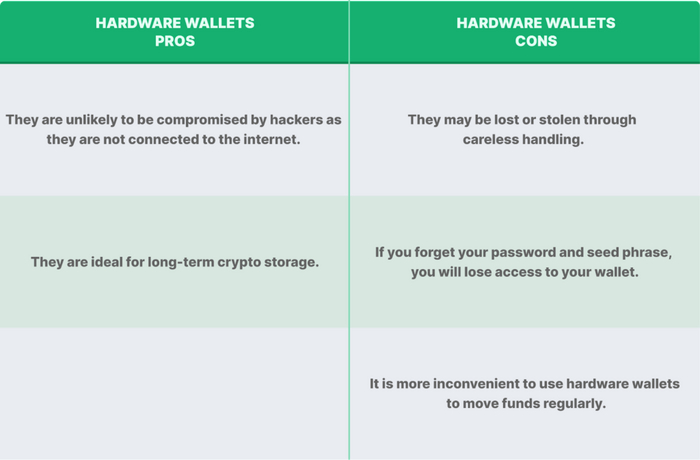
A cold or hardware wallet is a physical device that stores your private keys offline, costing anywhere between $50 and $250. Cold wallets are the most secure type of crypto wallet, as they are not connected to the internet and are therefore unlikely to be compromised by hackers (unless they have access to your private keys AND the hardware wallet).
Hardware wallets are physical devices that may resemble a USB stick or hard drives, which work by storing your pass codes, PINs and private keys on the device itself. In fact, even if the computer is infected with malware, the cold wallet remains safe as its private keys are held in a chip that never connects to the internet. So even if your computer is hacked or your online wallet is compromised, your coins will still be safe… unless your passcode and device are stolen.
However, as cold wallets are physical objects, that also opens them up to the risk of loss through careless handling. In the unfortunate event that your crypto hardware wallet is lost or stolen, you can use your seed phrase to regenerate your private keys. So remember to keep your seed phrases safe, offline, and on hard copy.
As cold wallets are ideal for long-term crypto storage, they’re better suited for hodling crypto than trading funds.
Ledger
Source: Ledger Nano X
Ledger is one of the most popular crypto hardware wallet providers, offering the Ledger Nano X, Ledger Nano S and the Ledger Nano S plus wallets. These devices are about the size of a thumb drive, running on the Ledger operating system called the Blockchain Open Ledger Operating System. It also has an in-built clear OLED display screen interface, and two navigation buttons for confirming transactions.
Ledger comes complete with a Ledger Live mobile app and a high level of security with its secure element chip used to store cryptographic data. Their flagship model, the Ledger Nano X, offers cryptocurrency compatibility of more than 5,500 tokens.
Trezor
Trezor is another well-known hardware wallet that offers the Trezor One and Trezor Model T. The Trezor Model T offers compatibility with 1,456 coins and tokens, and comes with the desktop, browser and Android Trezor Suite.
Trezor Suite is a user interface which lets you search and buy cryptocurrencies, manage your holdings, and send crypto securely. While this improves the user experience, there is the potential to introduce security vulnerabilities as you are using internet-enabled devices.
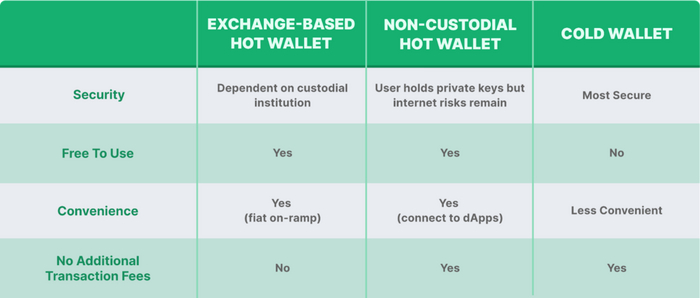
Considerations When Choosing a Wallet
Depending on your needs, you may opt for a hot wallet, a cold wallet, or both. We’ve summed up how the three types of wallets covered above compare against each other in this table:
Security
Security is a core feature when choosing a crypto wallet. Blockchain technology is known for its secure and immutable nature; ensuring your wallet has the best security features is necessary. Cold wallets are more secure than hot wallets since they are not always connected to the internet with exposure to potential cybersecurity risks like phishing or other hacks and scams. Besides, ensure your wallet has two-factor authentication (2FA) functionality to prevent unauthorized access to your assets.
Convenience
Since cold wallets store private keys offline, they involve plugging in physical devices and linking to web-based accounts to transfer funds. On the other hand, hot wallets live online; hence they are much easier to use for everyday transactions, like day trading.
Additional Transaction Fees
You’ll be still subjected to gas fees, regardless of whichever wallet you’re using. However, exchange-based wallets may include an additional charge that is derived from gas prices, although this fee may be waived if you are holding or staking the exchange’s native token. Before downloading or purchasing any wallet, check their service charges first.
Supported Coins
The wallet you plan to use may not support the coin you want to invest in. Some wallets support only one coin! Consider Mycelium, for instance. Despite having exceptional functionalities, it only supports Bitcoin. Therefore, be sure to check the wallet’s list of supported coins and tokensbefore using it to avoid disappointments.
Insurance
Some custodians provide asset insurance for users who incur losses through a technical problem or theft. Custodians differ in insurance policies, but selecting one that insures your assets in collaboration with a financial institution is advisable. For example, Binance provides insurance for USD deposits of up to $250,000 for U.S. customers. It has partnered with the Federal Deposit Insurance Corporation (FDIC) to implement this policy.
Using Hot and Cold Wallets to Manage Your Crypto Portfolio
Hot wallets are more convenient for daily use than cold wallets. On the other hand, cold wallets guarantee maximum security than hot wallets. Both wallets support a broad range of cryptocurrencies. Therefore, the ideal wallet for you relies on whether you prioritize the safety of your funds over the convenience of using a wallet regularly.
You can enjoy both benefits by combining both methods. For instance, you can hold a small percentage of funds in a hot wallet for trading purposes and keep the rest of your funds in a cold wallet as a long-term investment.
As a blockchain network participant, o party can rely on so-called “wallets” to manage its accounts and interaction with the blockchain. A party has multiple keys.
Problem
A party’s wallet is vulnerable to malicious attacks leading to key theft. If compromised, an attacker can use the key to issue transactions in that party’s identity. How to prevent the compromisation of keys?
Forces:
Security – A key may be hacked when being stored in a device, especially when connected to the Internet.
Usability – Some keys may be frequently used by blockchain participants while other keys may be used infrequently or might act as backup.
Solution
Users can choose to store keys in 2 types of wallets, namely hot wallet and cold wallet. Hot wallet typically refers to the blockchain gateways that are connected to the Internet.
Benefits
Secure storage – Cold wallets are isolated from the Internet; hence, provide secure storage for keys.
Usability – Such a secure storage also preserves the usability of keys, as once a cold wallet is connected to the Internet (either directly or via a middleware), a party can utilise those keys.
Drawbacks
Security – Hot wallets store one’s secret keys online hence are more vulnerable to theft. A cold wallet becomes more vulnerable as soon as it is connected to the hot wallet to copy/migrate a key.
Usability – Cold wallets are more secure than hot wallets but less convenient to use, as the user has to connect to the cold wallet.
Related patterns
In master and sub key generation pattern master key can be kept in the cold wallet while sub-keys can be stored in hot wallet.
Key sharding pattern could be used in a wallet application to split and merge a key to minimise its compromise.
When being integrated into wallet applications, predefined delegates in delegate list pattern can replace key ownership of a compromised key.
Known uses
MyEtherWallet is a hot wallet with a graphical interface for instant payment and withdrawal in Ethereum.
Trezor is a cryptocurrency hardware wallet, designed to store and encrypt users’ coins, passwords, and other digital keys. It is a single-purpose computer with independent memory to save all private data.
Ledger provides hardware wallet products to stores users’ private keys in a secure hardware device, protecting the cryptocurrencies.
Explore the different crypto storage options
What are the pros and cons of each wallet?
A hot wallet refers to any cryptocurrency wallet connected to the internet. Generally, hot wallets are easier to set up, access, and accept more tokens. But they are also more vulnerable to hacker attacks, possible regulations, and other technical vulnerabilities.
Cold Storage refers to any cryptocurrency wallet that is not connected to the internet. Overall, a cold wallet is more secure, but it doesn’t accept as many cryptocurrencies as hot wallets.
Should I Get a Cold Wallet?
If you are going to own Bitcoin, Ethereum, or other cryptocurrencies worth more than $100, you could buy a cold wallet right now — this is how much it costs.
Maybe you’ve heard people say, “Bitcoin gives you this opportunity of being your own bank”? There are advantages and disadvantages to this responsibility. Generally, cryptocurrencies have fewer middleman fees, less messy banking regulations, etc. Still, it is your responsibility to ensure the safety.
In short, here’s an analogy that can help you: a hot wallet can be thought of as a pocket wallet that you walk around town with; a cold wallet is a bank deposit.
Pros & Cons of Hot Wallets
Using a hot wallet will give you the following benefits:
By entering your pin and access number into the wallet, you quickly access your coins.
The investment cost is lower.
It has an extensive portfolio of applications or software that function as a hot wallet.
You need to set a PIN code or a security code to use it.
They allow you to connect to any platform so you can operate and trade.
Using one of these wallets may have the following disadvantages:
Higher risk of theft as money is stored in the cloud and is more vulnerable to cyber crooks.
It needs to be connected to the internet all the time. Otherwise, it can’t be supported, so it could be a big problem if the internet connection fails.
Pros & Cons of Cold Wallets
Using this wallet will give you the following benefits:
This type of wallet works without the internet, giving you a high level of security since many thefts take place on the internet.
A cold wallet supports ERC20 or other tokens standards, which can support an unlimited number of tokens..
You need to set a PIN code or a security code to use it.
You can take your device anywhere.
Using one of these wallets may generate the following disadvantages:
There is a risk of losing your device.
You cannot trade with these types of devices.
You need to invest around $100 to get it.
Like any physical device, it is prone to failure, corruption, or reading problems.
Remember that if you want to trade, a hot wallet is the better option. Still, we recommend encrypting it as best you can and choosing the best software for the most significant security. On the other hand, if you are a non-trading investor and want the highest level of protection, a cold wallet will be a better choice.
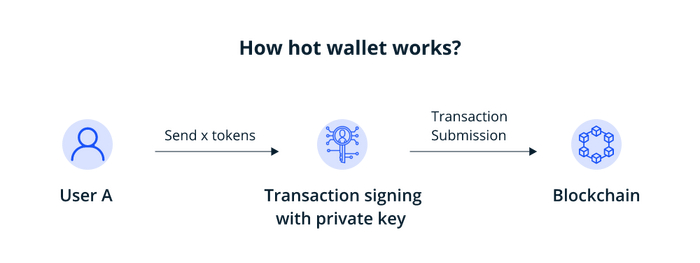
How does a hot wallet storage work?
When you install a hot wallet storage into your computer or device, it allows you to buy, send and receive crypto assets without really holding any crypto. Rather it holds the private keys using which a user can initiate transactions. This is possible, as it interacts with the blockchain storing your assets.
Metamask is one of the most popular hot wallets available today. So, we will explain how a hot wallet works using Metamask.
Metamask is available as a web browser extension that acts as a bridge between the blockchain, especially Ethereum, and your browser. When you download and install Metamask and add it as your browser extension, you will be asked to either ‘import wallet’ or ‘create a wallet.’ Import wallet allows you to add an existing wallet by typing a secret recovery phrase, while the latter enables creating a new crypto wallet.
How does hot and cold wallet interact?
As all of the funds that are transferred to you come to your receiving wallet, there are chances of crypto accumulation in your receiving wallet, resulting in crypto vulnerabilities. So, you need to send most of it to the cold wallet and some to the sending wallet. You need to have a minimum amount in your receiving wallet to transfer to the sending wallet once it falls short of cryptos, and this ensures that the sending wallet has enough cryptos whenever needed. However, suppose funds are not reliably coming to the receiving wallet, and the sending wallet urgently needs currencies. In that case, you can transfer the required amount from the cold wallet to the sending wallet.
How to mitigate crypto vulnerability?
Assume that you have a total of 200 ETH in your possession, and at any time, you want to avoid risking more than 30% of your funds. Based on this calculation, you need to set maximum and minimum thresholds per wallet to reduce the severity of any malware attack. So, the receiving wallet should have a minimum of 10 ETH and a maximum of 20 ETH. Similarly, the sending wallet should possess at least 20 ETH and up to 40 ETH. The rest of your assets should be kept in the cold wallet.
If you set a threshold for your sending and receiving wallets, adhere to it and ensure that the set amount does not exceed or drop down the limit. Excess funds are prone to vulnerabilities, and you cannot produce the required amount when needed if it is below the limit. So, always maintain an adequate amount of funds
How do hot and cold wallet setups in big systems work?
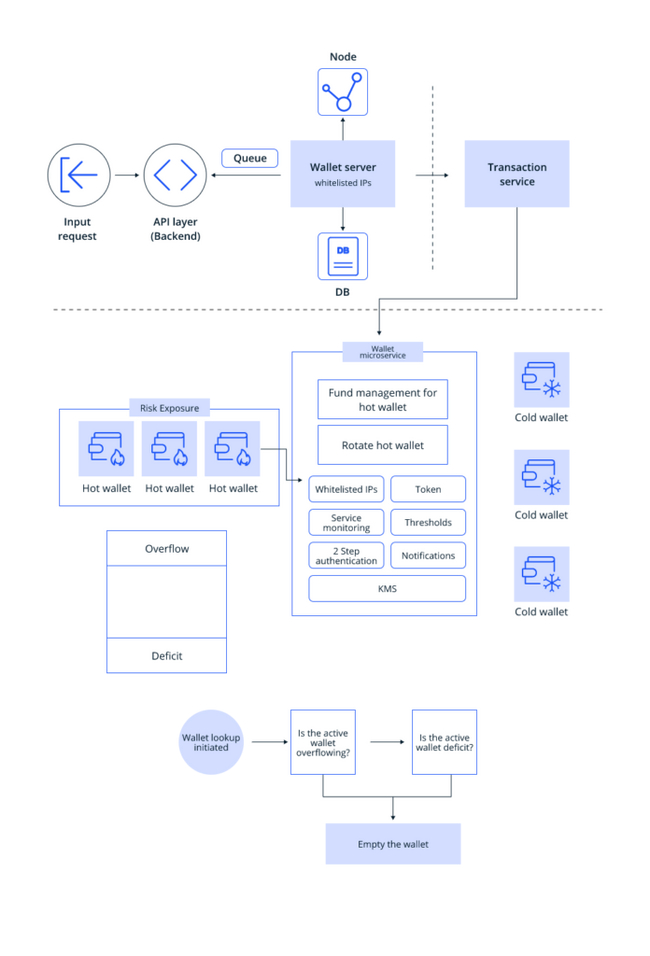
Hot and cold wallet setups vary, and each setup is designed based on the developer’s requirements and thought process. Through the following infographics, let us understand how hot and cold wallet setups are designed in big systems.
In the above-given infographic, if a person wants to send x number of tokens to another user, they input a request in the front end of the application, which is fetched in the API layer or the backend of the app. The backend transfers the input request to the wallet server. In a typical wallet architecture, a wallet server handles multiple microservices like managing nodes, databases, APIs or transaction services. As the user input, in this case, is related to the transaction service, the request is sent to this microservice.
The transaction service then sends the request to the wallet microservices, which handle all services related to the wallet. The wallet microservices can vary from platform to platform. In the above infographic, the wallet microservices include the following:
Fund management for the hot wallet – It ensures that it always sticks to its threshold without crypto overflow or deficit to prevent risk exposure.
Whitelisted IPs – It limits the number of people who can access your domain or server to a few trusted IP addresses permitted by you.
Token – It manages and keeps track of your tokens, like x number of ETH or x number of SOL.
Service monitoring – This microservice checks whether all services are working without glitches.
Thresholds – These ensure that you have the required amount in your wallet or not to send it to others.
2-step authentication – It is a security process where you have to verify your identity twice before accessing the wallet ecosystem.
Notifications – It alerts users on important matters like successful transaction completion notifications.
KMS – Key management system or KMS helps create, store, and manage it safely.
Rotate hot wallet
When the transaction input is transferred from the transaction service to the wallet microservices, all of the above microservices are carried out. Once all the services are done, and it is ascertained that your hot wallet has enough number of tokens, the x number of tokens is sent to the receiver. The transaction is, then, said to be successfully completed.
Conclusion
Merging both hot and cold wallets can help mitigate the risk of crypto attacks for both the users and the service providers. It acts as a comfortable middle ground by offering the benefits of both wallets, where one is used for crypto trading, and the other is used to hold the cryptos safely. Even though only hot wallets were popular during the initial days of crypto emergence, usage of cold wallets is getting more popular these days. Moreover, blending hot and cold wallets is gradually gaining prominence among crypto experts and service providers, owing to its huge benefits. Using just one wallet is, thus, outdated, and people gradually realize the advantages of combining both hot and cold wallets as an additional security measure.
Наконец-то меня, афериста, схватили за горло!!!!!!!!!!
Всем доброго!
Значит, ситуация. На днях, тридцатого ноября, оплатил в «КБ» покупку по QR-коду через приложение «Юмани». Пара пива к футболу и немного курева, ничего особенного. Пользуюсь я электронными кошельками редко, но тут пришлось это сделать. Банковской карты под рукой не было, а NFC не работает. Ну и ладно, оплата ведь прошла. Я хорошо провёл вечер и лёг спать.
И вот спустя шесть дней мне приходит письмецо от «Юмани». Говорят, кошелёк мой заблокирован, поскольку не понравился я службе безопасности. Ответным письмом прошу озвучить причину блокировки. Сперва мне поебали мозги, но со второй попытки я всё же выяснил причину блокировки. Пункт 4.21.8.3.
Что же это?
Вот:
К вопросу о работе техподдержки. Данное соглашение я почему-то искал самостоятельно, ведь в письме мне скинули ссылку на хуй пойми что. Ну да ладно.
Я сразу захотел узнать, а какого чёрта? Окей, я действительно редко пользуюсь этими кошельками, мне фиолетово и не так обидно, но блокировать клиента по такой причине? Вы, блядь, прикалываетесь?
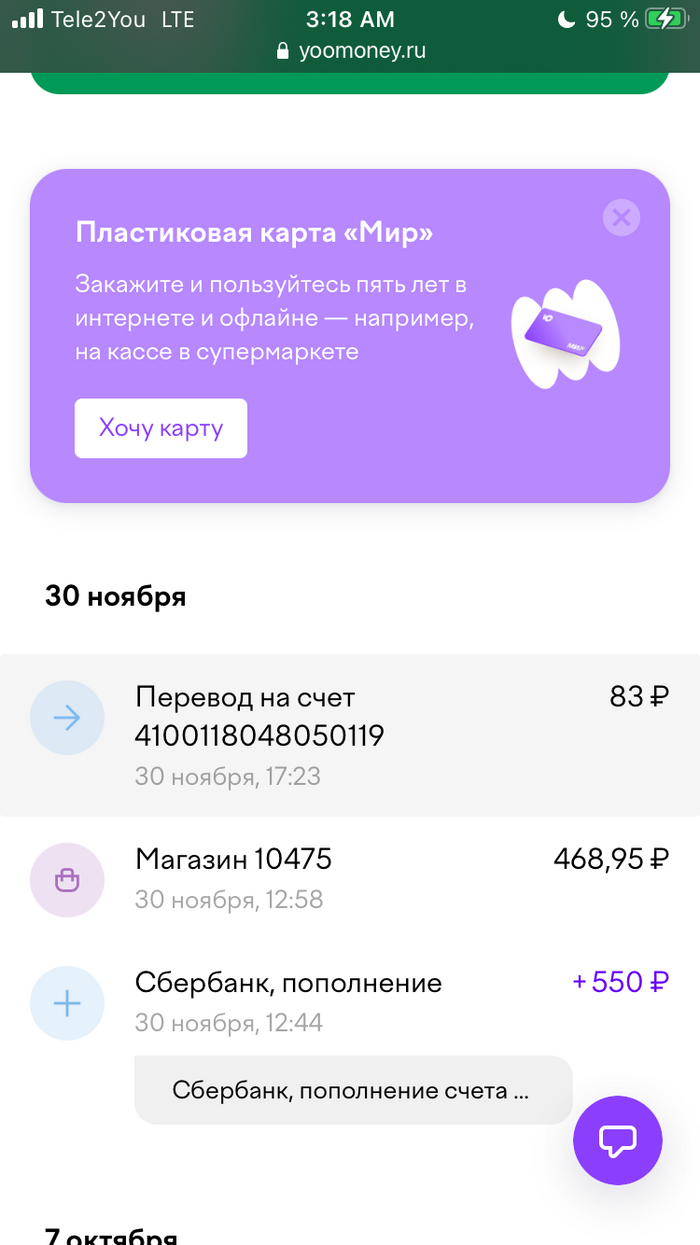
Вот, кстати, мои последние операции:
Какие СЛОЖНЫЕ СХЕМЫ ПРОВЕДЕНИЯ ОПЕРАЦИЙ служба безопасности могла тут увидеть? Неужели покупку в «КБ» или мощнейший перевод сестре 83-х рублей? Именно это я и спросил очередным ответным письмом. На что получил ответ, мол, всё правильно, ага, именно это мы и имели ввиду.
Брависсимо! Аферист больше никогда не купит пиво и курево!
Позволю себе отступить туда, в своё прошлое.
Я как-то работал в «Пятёрочке» и там была служба безопасности, естественно. А если быть точным - один мужик в пуловере и очках, навещавший наш магазин практически каждый день.
И вот этот пуловер называл себя Службой Безопасности. Что он делал? Проверял в компе все операции. От списания до прихода товара и так далее. Пытался понять - наёбываем мы его или нет. Мы его не наёбывали.
И в один замечательный день - зимой дело было - этот пуловер снова пришёл в магазин, но, как он сказал, не по делам. Подходит ко мне на кассу, выставляет с корзинки товары, я ему их пробиваю и он оплачивает покупку.
Перед ним и после него стояли другие покупатели. Пуловер ушёл. Всё окей. Всё зашибись.
Через пару минут пуловер и директор магазина подходят ко мне. Директор зовёт за кассу другого кассира, чтобы меня освободить. Ну ладно.
Этот пуловер достаёт из внутреннего кармана меховой куртки банку кофе, допустим «Нескафе», я кофе не пью, потому хуй знает что там ценится, а что нет. И вот он машет банкой «Нескафе» у меня перед лицом, говорит, что я плохо работаю, не слежу за сохранностью магазина (а не его ли это обязанность?). Просит меня написать объяснительную. Как же, мол, так, кассир сидит за кассой и не видит что там в другом конце магазина происходит?
Я ничего писать не стал. Директор вроде как «отмазал» меня.
Я тут конкретно зачесал языком, знаю. Но уж сильно мне служба безопасности «Юмани» напомнила того пуловера из службы безопасности «Пятёрочки».
Ребята из «Юмани», если вам нехуя делать на работе, почитайте книжку, посмотрите китайское порно (жутко-смешно), в конце концов, ёбаный пасьянс разложите. Зачем вы мешаете своим клиентам пользоваться вашим продуктом?